Onboarding Security Assessment plan
Instructions:
- Fill out all the headings and sub-headings.
- Remove all the instructional texts in italics before publishing.
- Attach additional documents as annexures to this report as applicable.
- Save the final copy of this report as a future reference.
Glossary:
| AppArmor | AppArmor is a Linux kernel security module that enables system administrators to restrict the capabilities of programs through per-program profiles. It is a Mandatory Access Control (MAC) system that complements Unix Discretionary Access Control (DAC) by permitting profiles to specify capabilities, including network access and file permissions. |
| ARP | ARP stands for Address Resolution Protocol. It is a protocol that helps computers on a network to find each other and also translate IP addresses, which are used to identify devices on the internet, to MAC addresses, which are used to identify devices on a local network. |
| CIS | CIS stands for the Center for Internet Security. The Center for Internet Security (CIS) is a non-profit organization that develops security best practices and standards, including the CIS Controls—a set of prioritized security best practices designed to defend against cyber threats. |
| ClamAV | ClamAV is an open-source antivirus software toolkit capable of detecting many types of malwares, including viruses, trojans, worms, and spyware. ClamAV is a free and open-source antivirus software toolkit available for Linux, Unix, Windows, and macOS. It is used by many organizations to protect their networks and systems from malware. |
| CONFIG_KEXEC | CONFIG_KEXEC is a kernel configuration option that enables the kexec system call. The kexec system call allows the kernel to load and boot another kernel without restarting the system. CONFIG_KEXEC is a powerful tool, but it is important to use it carefully. |
| CONFIG_STRICT_DEVMEM | CONFIG_STRICT_DEVMEM is a Linux kernel configuration option that enables strict access to the /dev/mem device. It is a security measure that can help to protect your system from unauthorized access and malwares. This means that only user-space access to memory-mapped peripherals is allowed, preventing user-space from accessing kernel memory or other user-space memory. |
| eCryptfs | eCryptfs is a Linux kernel filesystem that provides on-the-fly encryption of files and directories. It is a transparent encryption layer between the user and the underlying filesystem, encrypting and decrypting data as it is read and written. |
| GDPR | The General Data Protection Regulation (GDPR) is a regulation in EU law on data protection and privacy for all individuals within the European Union (EU) and the European Economic Area (EEA). GDPR applies to all organizations that process the personal data of individuals located in the EU, regardless of where the organization is located. |
| HIPPA | HIPAA stands for the Health Insurance Portability and Accountability Act. It is a federal law in the United States that protects the privacy of individually identifiable health information (PHI). HIPAA applies to healthcare providers, health plans, and healthcare clearinghouses that transmit or store PHI electronically. |
| IPtables | It is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall, implemented as different Netfilter modules. |
| IPv4 | Internet Protocol version 4 is the fourth version of the Internet Protocol. It is one of the core protocols of standards-based internetworking methods on the Internet and other packetswitched networks. |
| IPv6 | IPv6 is the next generation of the Internet Protocol (IP), with a 128-bit address space that solves the problem of IPv4 address exhaustion |
| Kexec | Kexec is a Linux kernel system call that allows you to load and boot a new kernel from the currently running kernel works by loading the new kernel into memory and then jumping to it. This process is very fast, and it does not require any user interaction |
| LDAP | LDAP stands for Lightweight Directory Access Protocol. It is a standard protocol for accessing and maintaining distributed directory information services. LDAP is a powerful directory management tool for cloud computing environments. |
| LVM | LVM stands for Logical Volume Management. It is a system for managing logical volumes on physical storage devices. LVM allows you to create, resize, and delete logical volumes on the fly without repartitioning your disks. LVM is often used in cloud computing environments |
| NetBIOS | NetBIOS stands for Network Basic Input/Output System. It is a networking standard that allows devices on a local area network (LAN) to communicate with each other. NetBIOS is used in a variety of applications, including file sharing, printing, and messaging. It is also used in some cloud computing applications. |
| NIST 800-53 | NIST 800-53 is a special publication from the National Institute of Standards and Technology (NIST) that provides a catalog of security and privacy controls for information systems and organizations. It is a widely used framework for assessing, selecting, and implementing security controls to protect against a broad range of threats and risks. |
| OpenVAS | OpenVAS, or Open Vulnerability Assessment System, is a free and open-source vulnerability scanner. It is a comprehensive tool that can be used to scan for vulnerabilities on a wide range of devices and systems, including servers, workstations, and networks. OpenVAS can be used to identify security vulnerabilities, such as software vulnerabilities, misconfigurations, and weak passwords. |
| OSINT | Open-source intelligence (OSINT) is the collection and analysis of publicly available information to produce intelligence. OSINT is the collection and analysis of publicly available information to gain insights into individuals, organizations, and events. It is increasingly being used by businesses, law enforcement, and intelligence agencies. |
| PCI DSS | PCI DSS stands for Payment Card Industry Data Security Standard. PCI DSS is a set of security standards that protect credit card data from theft and fraud. It applies to all organizations that handle credit card data, including cloud service providers. |
| SAML 2.0 | SAML 2.0 is an XML-based standard for exchanging authentication and authorization data between parties. SAML 2.0 is a powerful authentication and authorization standard used in cloud computing, SSO, and identity federation. |
| Seccomp_filter | Seccomp_filter is a Linux kernel feature that allows you to restrict the system calls that a process can make. This can be used to improve the security of your applications by preventing them from making system calls that they do not need to make. It works by using a Berkeley Packet Filter (BPF) program to filter out system calls. |
| Service Level Agreement (SLA) | It is a formal contract or agreement between a service provider and a customer that outlines the specific level of service, performance standards, and expectations that the provider will deliver. SLAs are commonly used to define the quality and reliability of services, including response times, uptime, and support availability. |
| SIEM | SIEM stands for Security Information and Event Management. SIEM systems collect, analyze, and respond to security events in real-time, helping organizations detect and respond to security threats. |
| SMB | SMB stands for small and medium-sized business. It is a term used to describe businesses that have fewer employees and lower revenue than large corporations. SMBs are the backbone of the global economy, and they play a vital role in creating jobs and stimulating economic growth. |
| Syscal | Syscal is a suite of geophysical instruments and software developed by IRIS Instruments. It is used to measure electrical resistivity and chargeability, which are the sub-surface's physical properties, and to monitor changes in the subsurface over time, such as the movement of groundwater or the stability of slopes. |
| SYSCTL | SYSCTL stands for System Control. It is a kernel mechanism that allows users to read and modify kernel parameters at runtime. SYSCTL is used to control a wide variety of kernel parameters, such as network settings, memory management settings, and security settings. |
| Terms of Service (TOS) | It refers to a legal agreement that outlines the rules, conditions, and obligations that users must adhere to when using a particular service, website, or platform. TOS agreements often cover topics such as user behavior, privacy policies, content usage, and dispute resolution. Users typically need to accept these terms before using the service. |
| TPM | TPM (Trusted Platform Module) is a secure crypto-processor that is built into hardware to protect your device from unauthorized access and malicious software. It is used in a variety of devices, including laptops, desktops, servers, and mobile devices. It is also used in cloud computing to protect customer data |
| TSC SOC2 | TSC SOC2 stands for Trust Services Criteria and Service Organization Control 2. SOC 2 is a security framework developed by the AICPA to help organizations assess and report on the security, availability, processing integrity, confidentiality, and privacy of customer data in the cloud. |
| UNIX | UNIX is a family of multitasking, multi-user computer operating systems that derive from the original AT&T Unix, whose development started in 1969 at the Bell Labs research center by Ken Thompson, Dennis Ritchie, and others. UNIX is a powerful and versatile operating system used in a wide range of environments, including servers, workstations, desktops, and specialized applications. |
| USBauth | USBauth is a tool that can be used to implement a firewall for USB devices on Linux systems. USBauth is a USB firewall that allows users to define rules that specify which USB devices are allowed to access the system. It is a simple tool that can be used to protect against malware, data exfiltration, and denial-of-service attacks. |
| USBGuard | USBGuard is a software framework for implementing USB device authorization policies as well as the method of use policies. USBGuard works by creating a whitelist of authorized USB devices. This whitelist can be created based on the device's vendor ID, product ID, or other criteria. Once the whitelist is created, only USB devices on the whitelist will be allowed to be used on the system. |
| user-setup/encrypt-home=true | user-setup/encrypt-home=true is a preseed option in Ubuntu that encrypts the home directory of the first user account created during installation. This security measure helps protect the user's data from unauthorized access, even if the attacker has the user's password. |
| Wazuh | Wazuh is an open-source security information and event management (SIEM) solution that helps organizations detect, investigate, and respond to security threats. Wazuh collects and analyzes security data from a variety of sources to identify and respond to security threats. |
| XDR | XDR, or Extended Detection and Response, is a cybersecurity solution that unifies security data and analytics across multiple sources to provide a holistic view of threats and incidents. This allows security teams to detect, investigate, and respond to threats more quickly and effectively. |
Objective: The objective of this cyber security assessment is to evaluate the security readiness of our new customers, identify potential vulnerabilities, and ensure that their cloud services deployment aligns with our security standards and best practices.
1. Pre-Assessment Preparation
1.1 Customer Information
1.1.1 Customer Primary Contact Information
Name of the Company: Address:
| SI | Name | Designation | Email Address | Phone # |
|---|---|---|---|---|
1.1.2 Organization Overview
Gather information about the customer’s organization, including its industry, size, and locations. Are there any subsidiaries or affiliates that will be using Meghna Cloud services?
1.1.3 Cloud Service Usage
Identify the specific cloud services offered by Meghna Cloud that the customer intends to use. This may include compute resources, storage solutions, backup services, or a combination of these.
1.1.4 Scope of Assessment
Define the scope of the cybersecurity assessment within the context of the customer’s intended cloud service usage. Specify which systems, applications, or data will be included in the assessment.
1.1.5 Regulatory Requirements
If applicable, determine if the customer is subject to any specific industry regulations, compliance standards, or data protection requirements that may impact their cloud service deployment. Ensure alignment with Meghna Cloud’s TOS and Privacy Policy.
1.1.6 Existing Security Measures
Attach any existing security measures or policies the customer has in place related to their cloud services. This includes access controls, encryption practices, and incident response procedures.
1.1.7 Data Classification
Understand the categorization of customer data to be stored or processed within the Meghna Cloud environment. Recognize any critical or classified data types and the essential security measures.
1.1.8 Previous Security Incidents
Provide details of any previous security incidents or breaches the customer may have experienced, both related to their cloud services and in general. This information can help identify potential vulnerabilities.
1.1.9 Third-Party Services
Identify all third-party services, integrations, or partners that are part of the customer's cloud environment. Ensure compatibility and security considerations.
1.1.10 Documentation and Policies
Attach copies of relevant documentation, such as security policies, procedures, and network diagrams, to gain a comprehensive understanding of the customer's environment.
1.2 Legal and Compliance Review
1.2.1 Review of Agreements
Attach or provide reference to contract and SLA.
1.2.2 Data Privacy and Protection
Ensure that Meghna Cloud is in compliance with relevant data privacy and protection regulations, such as the General Data Protection Regulation (GDPR) for European customers or the Health Insurance Portability and Accountability Act (HIPAA) for healthcare customers or any specific regulatory instructions from the Government of Bangladesh.
1.2.3 Data Ownership and Residency
Clarify data ownership rights and data residency requirements. Ensure that the customer's data is stored and processed in accordance with their geographical and jurisdictional requirements.
2. Assessment Execution
2.1 Methodology
During the customer onboarding process, we undertake a complimentary general vulnerability assessment as an initial step to mitigate any potential security threats before any client data is introduced into our cloud environment. It is our priority to ensure that our clients' information remains secure from the outset.
Furthermore, we offer comprehensive security assessment and testing services upon client request. These services are designed to meticulously identify any misconfigurations or other security vulnerabilities that the client may wish to uncover and subsequently address. Our aim is to provide clients with the tools and insights necessary to fortify their security posture, thereby safeguarding their data and assets effectively.
2.1.1 Initial Vulnerability Assessment
Meghna Cloud is committed to ensuring the utmost security and protection of client data and applications. In our complementary initial vulnerability assessment for client onboarding, we provide a range of vital scans to thoroughly evaluate and fortify your network infrastructure. Our network-based scans delve into both wired and wireless networks, identifying potential security threats and vulnerabilities, including unauthorized devices and insecure connections. Our host-based scans meticulously examine servers, workstations, and network hosts, offering insights into configuration settings and update histories.
Additionally, we conduct wireless scans to pinpoint rogue access points, ensuring the secure configuration of your network. Our application scans meticulously examine websites, uncovering known software vulnerabilities and potential security issues in network and web application configurations. Lastly, our database scans identify weaknesses in database configurations, providing actionable recommendations to bolster your defenses. These scans can be executed in various ways, including external scans targeting internet-accessible infrastructure, internal scans fortifying networkaccessible systems, authenticated scans to view vulnerabilities from verified user perspectives, and unauthenticated scans simulating potential external threats, all tailored to ensure comprehensive security coverage for your organization.
2.1.2 Comprehensive Vulnerability Assessment
Our comprehensive vulnerability assessment services are designed for clients who require advanced security measures for regulatory compliance and/or compliance with industry specific benchmarks/standardizations. The details of our assessment approach are provided below. For pricing information of any comprehensive vulnerability assessment services, please contact with your Meghna Cloud point of contact or our sales team through info@meghnacloud.gov.bd.
2.1.2.1 VAPT
Based on network layer assessment report with common attacks and existing exploits
Vulnerability Assessment (for application layer):
Customized vulnerability assessment will be performed which will include the servers.
Advanced Penetration Testing:
Custom testing exploits will be developed by our experts based on discovered vulnerabilities.
2.1.2.2 Server Hardening
IPTables Configure:
Iptables is a user-space utility program that allows a system administrator to configure the IP packet filter rules of the Linux kernel firewall, implemented as different Netfilter modules. The filters are organized in different tables, which contain chains of rules for how to treat network traffic packets. Different kernel modules and programs are currently used for different protocols; iptables applies to IPv4, ip6tables to IPv6, ARPtables to ARP, and EBtables to Ethernet frames.
File & LVM encryption Enable:
Install or enable encrypted LVM, which allows all partitions in the logical volume, including swap, to be encrypted. Encrypted Private Directories were implemented, utilizing eCryptfs, in ubuntu as a secure location for users to store sensitive information. The server and alternate installers had the option to setup an encrypted private directory for the first user.
In Ubuntu, support for encrypted home and filename encryption was added. Encrypted Home allowed users to encrypt all files in their home directory and was supported in the Alternate Installer and also in the Desktop Installer via the pressed option user-setup/encrypt-home=true. Official support for Encrypted Private and Encrypted Home directories was dropped in Ubuntu LTS. It is still possible to configure an encrypted private or home directory, after Ubuntu is installed, with the ecryptfs-setupprivate utility provided by the ecryptfs-utils package.
SYSCTL configure with Syscall filtering and block Kexec:
Programs can filter out the availability of kernel syscalls by using the seccomp_filter interface. This is done in containers or sandboxes that want to further limit the exposure to kernel interfaces when potentially running untrusted software. It is now possible to disable kexec via sysctl. CONFIG_KEXEC is enabled in Ubuntu so end users are able to use kexec as desired and the new sysctl allows administrators to disable kexec_load. This is desired in environments where CONFIG_STRICT_DEVMEM and modules_disabled are set, for example. When Secure Boot is in use, kexec is restricted by default to only load appropriately signed and trusted kernels.
Usbguard:
Usbguard package has been available in universe to provide a tool for using the Linux kernel's USB authorization support to control device IDs and device classes that will be recognized.
Usbauth:
Usbauth package has been available in universe to provide a tool for using the Linux kernel's USB authorization support, to control device IDs and device classes that will be recognized. Additionally, the following will be ensured from Meghna Cloud:
- AppArmor configure with all security packages
- Server patch update after the assessment
- Device restriction
- Access log monitoring
- TPM Enable
2.1.2.3 Security Information and Event Management (SIEM)
Wazuh aggregates, stores, and analyzes security event data to identify anomalies or indicators of compromise. The SIEM platform adds contextual information to alerts to expedite investigations and reduce average response time. It scans the systems against the Center for Internet Security (CIS) benchmark to allow to identify and remediate vulnerabilities, misconfigurations, or deviations from best practices and security standards. It also helps to track and demonstrate compliance with various regulatory frameworks such as PCI DSS, NIST 800-53, GDPR, TSC SOC2, and HIPAA.
Wazuh prioritizes identified vulnerabilities to speed up the decision-making and remediation process. The Wazuh vulnerability detection capability ensures to meet regulatory compliance requirements while reducing the attack surface. Wazuh correlates events from multiple sources, integrates threat intelligence feeds, and provides customizable dashboards and reports. It can customize alerts to meet specific requirements. This allows security teams to respond quickly to threats and minimize the impact of security incidents. Wazuh allows to generate comprehensive, actionable information that meets all unique needs. It reports to demonstrate compliance with various regulations and standards.
2.1.2.4 Extended Detection and Response (XDR)
Wazuh offers several advantages as an open-source XDR platform. It is customizable and can be modified to meet specific needs, giving greater flexibility and control over environment. It has a large community of users and developers who provide support and expertise. Furthermore, it integrates with a broad range of security solutions, allowing to create a comprehensive security ecosystem.
The Wazuh behavioral analysis capabilities involve using advanced analytics to identify deviations from normal behavior, which may indicate potential security threats. These capabilities include monitoring file integrity, network traffic, user behavior, and anomalies in system performance metrics.
Wazuh maps detected events to the relevant adversary tactics and techniques. It also ingests third-party threat intelligence data and allows to create custom queries to filter events and aid threat hunting. It automatically responds to threats to mitigate the potential impact on infrastructure and built-in response actions or create custom actions according to incident response plan. It has a built-in integration with cloud services to collect and analyze telemetry.
It protects native and hybrid cloud environments including container infrastructure by detecting and responding to current and emerging threats. It integrates with threat intelligence sources, including open-source intelligence (OSINT), commercial feeds, and user-contributed data to provide up-to-date information on potential threats.
Wazuh agent runs on the most common operating systems to detect malware, perform file integrity monitoring, read endpoint telemetry, perform vulnerability assessment, scan system configuration, and automatically respond to threats. It ingests telemetry via syslog or APIs from third-party applications, devices, and workloads like cloud providers and SaaS vendors.
2.1.2.5 Auto VA Platform
OpenVAS is a fully featured Vulnerability Management Software designed to serve Agencies, Enterprises. OpenVAS provides end-to-end solutions designed for end-users. This online Vulnerability Management system offers Prioritization, Asset Tagging, Web Scanning, Asset Discovery, Risk Management at one place.
Wazuh prioritizes identified vulnerabilities to speed up the decision-making and remediation process. The Wazuh vulnerability detection capability ensures to meet regulatory compliance requirements while reducing the attack surface.
2.1.2.6 Endpoint Protection
Files will be scanned quickly due to amazing optimization. ClamAV is able to detect millions of viruses, worms, ransomwares, trojans, mobile malware, and even Microsoft Office macro viruses. Real-time protection is only available for Linux systems. ClamScan or ClamD provides an option for blocking the file access until it has been scanned for malware. Signature databases will ensure that only trusted databases will be used by ClamAV. It is also able to scan archives and compressed files. It detects any suspicious files; it automatically sends them to the cloud sandbox for further analysis so that they cannot perform any malicious activity.
2.1.2.7 Data Loss Prevention
OpenDLP is a free and open source, agent- and agentless-based, centrally managed, massively distributable data loss prevention tool released under the GPL. Given appropriate Windows, UNIX, MySQL, or MSSQL credentials, OpenDLP can simultaneously identify sensitive data at rest on hundreds or thousands of Microsoft Windows systems, UNIX systems, MySQL databases, or MSSQL databases from a centralized web application.
OpenDLP has two components:
- A web application to manage Windows agents and Windows/UNIX/database agentless scanners
- A Microsoft Windows agent used to perform accelerated scans of up to thousands of systems simultaneously.
The web application automatically deploys and starts the agents over Netbios/SMB. When done, it automatically stops, uninstalls, and deletes the agents over Netbios/SMB. For a better overview, it performs the following:
- Pauses, resumes, and forcefully uninstalls agents in an entire scan or on individual systems
- Concurrently and securely receives results from hundreds or thousands of deployed agents over two-way-trusted SSL connection
- Creates Perl-compatible regular expressions (PCREs) for finding sensitive data at rest
- Creates reusable profiles for scans that include whitelisting or blacklisting directories and file extensions
- Reviews findings and identify false positives
- Exports results as XML
- Writes in Perl with MySQL backend
- Deploys Windows agents through existing Meterpreter sessions (new in 0.5)
The agent performs the following activities:
- Runs on Windows 2000 and later systems
- Writes in C with no .NET Framework requirements
- Runs as a Windows Service at low priority so users do not see or feel it
- Resumes automatically upon system reboot with no user interaction
- Securely transmit results to web application at user-defined intervals over two-way-trusted SSL connection
- Uses PCREs to identify sensitive data inside files
- Performs additional checks on potential credit card numbers to reduce false positives
- It can read inside ZIP files, including Office 2007 and OpenOffice files
- It limits itself to a percent of physical memory so there is no thrashing when processing large files
Agentless Database Scans:
In addition to performing data discovery on Windows operating systems, Open DLP also supports performing agentless data discovery against the following databases: Microsoft SQL server MySQL
Agentless File System and File Share Scans:
With Open DLP 0.4, one can perform the following scans:
- Agentless Windows file system scan (over SMB)
- Agentless Windows share scan (over SMB)
- Agentless UNIX file system scan (over SSH using sshfs)
2.1.2.8 Identity and Access Management
Single-Sign On:
Users authenticate with Keycloak rather than individual applications. This means that your applications do not have to deal with login forms, authenticating users, and storing users. Once logged-in to Keycloak, users do not have to login again to access a different application.
This also applies to logout. Keycloak provides single-sign out, which means users only have to logout once to be logged-out of all applications that use Keycloak.
Identity Brokering and Social Login:
Enabling login with social networks is easy to add through the admin console. It is just a matter of selecting the social network you want to add. No code or changes to your application is required.
Keycloak can also authenticate users with existing OpenID Connect or SAML 2.0 Identity Providers. Again, this is just a matter of configuring the Identity Provider through the admin console.
User Federation:
Keycloak has built-in support to connect to existing LDAP or Active Directory servers. You can also implement your own provider if you have users in other stores, such as a relational database.
Admin Console:
Through the admin console administrators can centrally manage all aspects of the Keycloak server. They can enable and disable various features. They can configure identity brokering and user federation. They can create and manage applications and services and define fine-grained authorization policies. They can also manage users, including permissions and sessions.
Account Management Console:
Through the account management console users can manage their own accounts. They can update the profile, change passwords, and setup two-factor authentication. Users can also manage sessions as well as view history for the account. If you've enabled social login or identity brokering users can also link their accounts with additional providers to allow them to authenticate to the same account with different identity providers.
Standard Protocols:
Keycloak is based on standard protocols and provides support for OpenID Connect, OAuth 2.0, and SAML.
Authorization Services:
If role-based authorization doesn't cover your needs, Keycloak provides fine-grained authorization services as well. This allows you to manage permissions for all your services from the Keycloak admin console and gives you the power to define exactly the policies you need.
2.1.2.9 Intrusion Prevention Systems
Snort is the foremost Open Source Intrusion Prevention System (IPS). Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users. Snort can be deployed inline to stop these packets, as well. Snort has three primary uses: As a packet sniffer like tcpdump, as a packet logger — which is useful for network traffic debugging, or it can be used as a full-blown network intrusion prevention system.
2.1.2.10 VPN
It works in any configuration including remote access, site to site VPNs, Wi-Fi security and enterprise scale access solutions. It has features like load balancing, failover and access controls. It can tunnel IP sub-networks or virtual Ethernet adapters. Open VPN benefits are: Supports perfect forward secrecy, has firewall compatibility and Better Security (256-bit encryption keys).
2.1.2.11 Security Analyst Consultation
Meghna Cloud has a dynamic security team with a wide array of expertise and experience, both internationally and domestically. Our competent security analysts are able to provide on-site and offsite, 24/7/365 service being fully committed to secure client assets and fulfill their requirements.
2.2 Findings and Remediation
2.2.1 Assessment Results
Attach all findings and observations from the security assessments, including vulnerabilities, weaknesses, and compliance gaps. Ensure that findings are categorized and prioritized based on severity in Risk Assessment Section-3.
2.2.2 Finding Reports
Please attach all generated reports as annexure to this document.
2.2.3 Remediation Plan
Collaborate with the customer to develop a remediation plan. The plan should include:
- Prioritization of findings based on risk (Section-3).
- Detailed steps to address each finding.
- Responsible parties for remediation.
- Timelines for completion.
3. Risk Assessment
Meghna Cloud will use a systematic approach to assess risks, taking into account both qualitative and quantitative factors. The assessment will consider the following key elements:
3.1 Threats and Vulnerabilities
Refer to the Findings and Remediation (Section 2.2) for a list of identified threats and vulnerabilities.
3.2 Risk Scoring
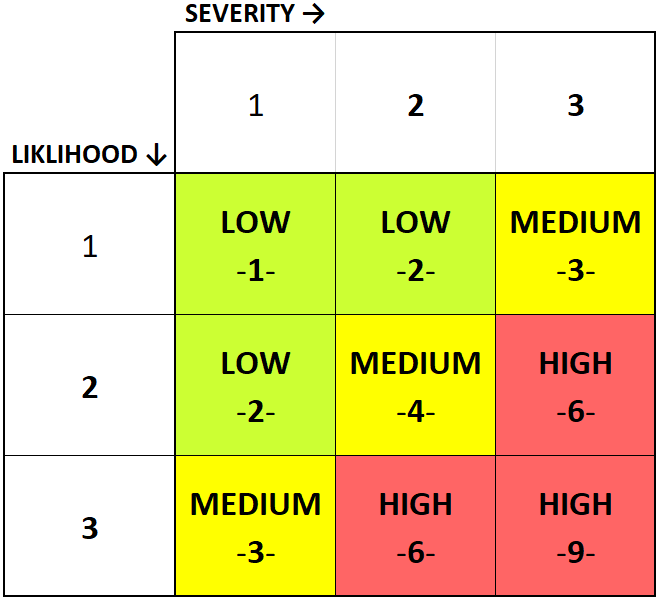
3.3 Impact Assessment
Evaluate the potential impact of each threat on the confidentiality, integrity, and availability of Meghna Cloud's services and the customer's data. Consider the following:
- Financial impact.
- Reputational damage.
- Legal and regulatory consequences.
- Customer data exposure.
- Likelihood Assessment:
- Assess the likelihood of each threat materializing. This assessment should take into account historical data, security controls in place, and any emerging trends or threats in the cybersecurity landscape.
| SI | Detail of Threat | Impact | Risk Score |
|---|---|---|---|
| 1 | include the details of the identified threat here | include the impact of the threat | provide a score for the threat, following the risk score |
| 2 | ... | ... | ... |
Table 3.2: Impact Assessment Table
3.4 Risk Mitigation
List the mitigation plan for high priority risks identified.
3.5 Risk Communication
All risk and mitigation strategies should be communicated to all stakeholders
| SI | Stakeholder Name & Designation | Email ID | Phone Number |
|---|---|---|---|
Table 3.3: Risk Communication Table
4. Post-Assessment Review
4.1 Validation Testing
After remediation, perform validation testing to confirm that the identified issues have been successfully resolved. Ensure that there are no unintended consequences of remediation efforts. Attach validation testing reports and confirmation for remediation.
4.2 Continuous Monitoring
List continuous monitoring measures taken to detect and respond to security threats and incidents. Mention periodic review plans.
4.3 Lessons Learned
List the lessons learned to identify improvements in the assessment process and areas for continuous security enhancement.
4.4 Closure
Share this finalized report with relevant stakeholders for transparency and accountability.